Getting your remote devices to talk with your cloud services in a way that feels truly safe is a big deal, right? You want to make sure every bit of information, especially the really private stuff, goes where it needs to go without any unwelcome peeking or tampering. It's a bit like sending those very important financial papers or confidential files; you want a trusted method for them to arrive, and that's exactly what we aim for when we securely connect remote IoT devices to your AWS VPC.
For many businesses, the idea of devices out in the world, perhaps gathering sensitive readings or managing important operations, sending their information back home can feel a little worrying. You worry about who might be listening in, or if the data could get changed along the way. Just like you'd want to encrypt an email attachment or use a secure link for sharing files, your IoT setup needs that same level of care. It's about building trust in your digital connections, and that, you know, is pretty important.
This article will walk you through the key ideas and methods for making sure your internet-connected things, those remote IoT gadgets, can communicate with your private cloud network on AWS in a very protected way. We will look at why security is so important, some common ways to set up these connections, and what practices help keep everything safe. So, let's get into how you can give your IoT data a really safe trip home.
Table of Contents
- Why Security Matters for Your Remote IoT
- Common Ways to Securely Connect Remote IoT to AWS VPC
- Essential Security Practices for IoT Connectivity
- Making the Right Choice for Your Setup
- Frequently Asked Questions (FAQ)
Why Security Matters for Your Remote IoT
When you have devices out in the world, collecting information or taking actions, their connection back to your main system is a pretty big deal. Think about it: if someone could mess with those connections, they might get their hands on your private information or even control your devices. That's why making sure you securely connect remote IoT devices to your AWS VPC is so very important. It's about protecting your operations and your reputation, too.
The risks are real, honestly. An unprotected connection could let unwanted people see what your devices are doing, or worse, put bad instructions onto them. This could lead to all sorts of trouble, from data leaks to machines not working right. So, we really need to think about how to keep those pathways safe and sound, in a way that makes sense for your business, and that's just a little bit of what we're talking about here.
The Heart of the Matter: Data Protection
The information your IoT devices gather can be incredibly valuable, or it might be very sensitive. Perhaps it's patient health information, or details about a manufacturing process. Whatever it is, you want to make sure it stays private. So, protecting this data as it moves from the device to your AWS VPC is, you know, absolutely essential. It's like putting your confidential documents in a very strong, locked box before sending them.
Any weakness in this data's trip could mean it falls into the wrong hands. This could lead to big problems, like privacy breaches or competitive disadvantages. We are talking about making sure every piece of data is treated with the care it deserves, so it gets to its destination just as it should be. This is a primary concern for anyone dealing with IoT, in some respects.
Keeping Things Private: Network Isolation
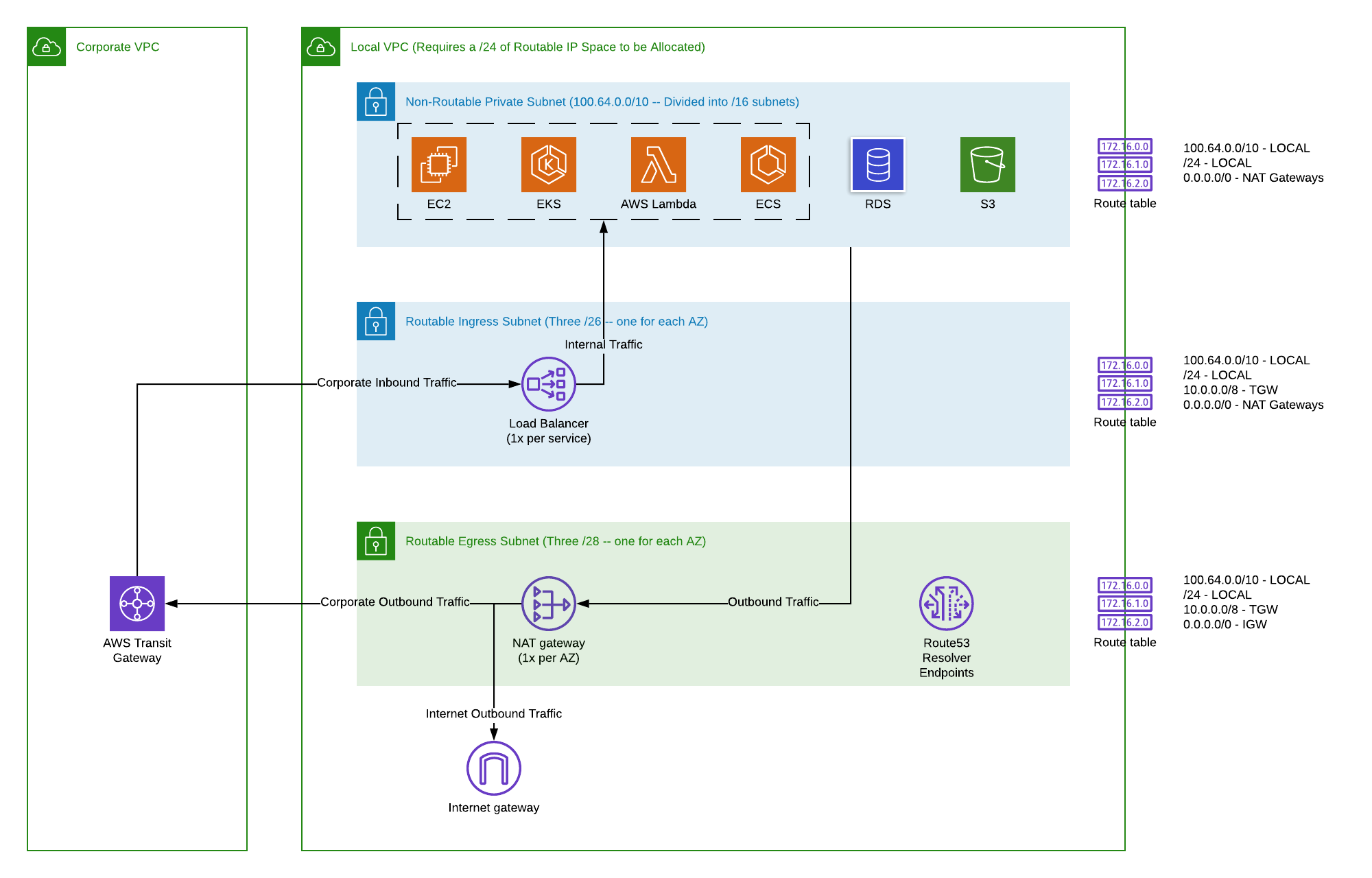
Your AWS Virtual Private Cloud, or VPC, is like your own private section of the internet inside AWS. It's a place where your servers and applications can live, separate from everyone else's. When you connect your IoT devices directly into this private space, you're essentially giving them a special, protected entrance. This helps keep them away from the wider internet's dangers, which is a good thing, really.
Without this isolation, your devices might be more open to attacks or unwanted attention. By bringing them into your VPC, you add a layer of security that helps control who can talk to them and what information can flow. It's about creating a safe little bubble for your IoT operations, which, honestly, makes a lot of sense.
Common Ways to Securely Connect Remote IoT to AWS VPC
There are a few main paths you can take to securely connect remote IoT devices to your AWS VPC. Each method has its own benefits, and the best choice often depends on what your devices do, how much data they send, and your overall security needs. We will look at some of the most popular options, so you can get a better idea of what might work for you, basically.
Choosing the right connection method is a pretty big decision. It affects not just security but also how well your system performs and how much it might cost. So, understanding these different ways is a really good first step. It helps you pick a solution that fits your specific situation, and that's what we want, right?
VPN Connections: A Trusted Path
One very common way to securely connect remote IoT devices to your AWS VPC is by using a Virtual Private Network, or VPN. Think of a VPN as creating a secure, encrypted tunnel over the public internet. Your IoT device sends its data through this tunnel, and it comes out safely inside your VPC. This method is, you know, quite popular for its reliability.
Setting up a VPN connection typically involves configuring a VPN client on your IoT device or a gateway device near your IoT fleet, and then setting up a VPN server or gateway within your AWS VPC. It provides a private link, making it much harder for anyone to snoop on your data as it travels. This is a pretty straightforward way to add a lot of security, especially for devices that need constant, private communication, and stuff.
AWS IoT Core with VPC Endpoints: Direct and Private
AWS IoT Core is a service designed to help you connect and manage billions of IoT devices. A really neat feature for security is using VPC Endpoints with IoT Core. Instead of your devices talking to IoT Core over the public internet, a VPC Endpoint creates a private connection directly from your VPC to the IoT Core service. This means your data never leaves the AWS network, which is, honestly, a big plus for security.
When you use a VPC Endpoint, your devices can communicate with IoT Core as if it were right there in your private network. This significantly reduces the chances of data interception and makes your connection much more private. It's a very direct way to securely connect remote IoT devices to your AWS VPC, especially if you are already using AWS IoT Core for device management, you know.
Learn more about secure connections on our site, and link to this page for more details.
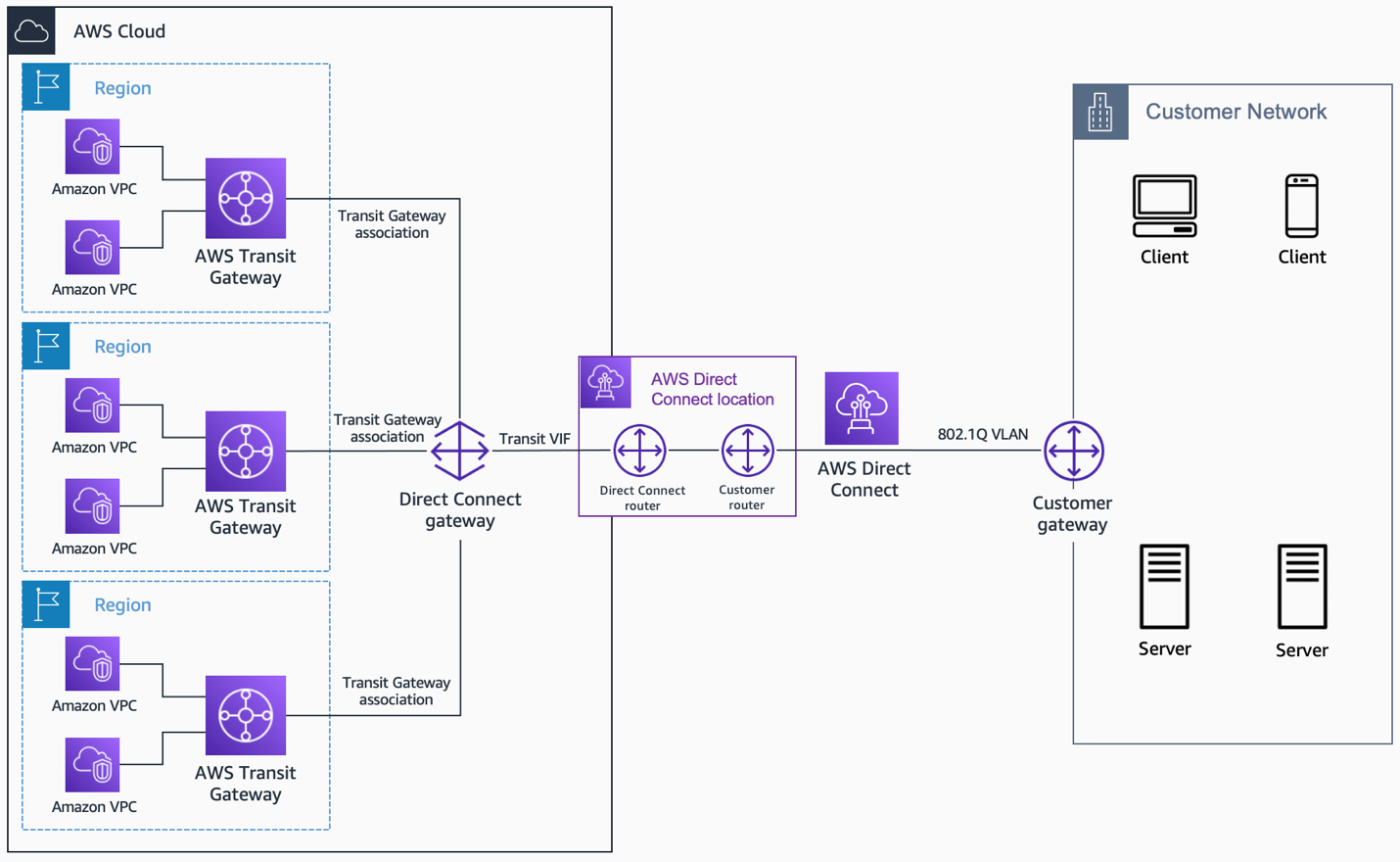
AWS Direct Connect: For the Big Data Movers
For situations where you have a lot of IoT devices in a specific location, or if they send truly massive amounts of data, AWS Direct Connect might be a good fit. This service creates a dedicated, private network connection from your on-premises location directly to AWS. It's not using the public internet at all, which is, in fact, a very high level of security and performance.
While Direct Connect is often used for connecting entire data centers to AWS, it can be really useful for large-scale IoT deployments where you need guaranteed bandwidth and very low latency. It's a more involved setup and typically costs more, but for very critical or high-volume IoT operations, it offers a pretty robust and secure pathway. It’s definitely something to consider for those bigger projects, you know.
Essential Security Practices for IoT Connectivity
Just choosing a secure connection method isn't the whole story. To truly securely connect remote IoT devices to your AWS VPC, you need to follow some key security practices. These practices add layers of protection, making your entire IoT system much harder for unwanted parties to mess with. They are, quite simply, very important for keeping your data and devices safe.
Thinking about security from every angle helps prevent problems down the road. It's about being proactive rather than reactive, which, as a matter of fact, is always a better way to go. Let's look at some of these important practices that help keep everything locked down.
Device Authentication and Authorization
Every single IoT device needs to prove it is who it says it is before it can connect to your AWS VPC or send data. This is called authentication. You also need to control what each device is allowed to do once it's connected; this is authorization. Using strong certificates or unique device IDs is a pretty common way to handle this, honestly.
Without proper authentication, any device could pretend to be one of yours and send bad data or try to access sensitive services. And without authorization, a device might do things it shouldn't, like access data it doesn't need. So, making sure only trusted devices can connect and only do what they are supposed to is, you know, absolutely critical for security.
Data Encryption: In Transit and At Rest
Even with a secure connection, encrypting your data adds another strong layer of protection. This means scrambling the data so that if someone *does* manage to get a hold of it, they can't read it without the right key. You need to encrypt data as it moves from the device to your VPC (in transit) and also when it's stored in your AWS services (at rest). This is a pretty standard security measure, you know.
For data in transit, protocols like TLS (Transport Layer Security) are typically used, which is what helps secure web browsing. For data at rest, AWS services like S3 or databases offer built-in encryption options. This double layer of encryption means your data is protected at every stage, which is, frankly, a very comforting thought.
Monitoring and Logging
You can't protect what you don't see. Setting up robust monitoring and logging for your IoT devices and their connections to your AWS VPC is extremely important. This means keeping a close eye on who is connecting, when, and what they are doing. If something unusual happens, you want to know about it right away, so you can act quickly. This is, in fact, a very proactive security step.
AWS provides services like CloudWatch and CloudTrail that can help you collect logs and set up alerts. By reviewing these logs regularly, you can spot potential security issues or strange patterns that might suggest an attack. It's about having visibility into your system, which, you know, helps you maintain control and respond effectively.
Making the Right Choice for Your Setup
Deciding how to securely connect remote IoT devices to your AWS VPC involves thinking about your specific needs. Consider how many devices you have, how much data they send, and how sensitive that data truly is. Also, think about your budget and how much effort you can put into setting things up. Each method has its own trade-offs, so a bit of careful thought is helpful, you know.
For smaller setups or those just starting, using AWS IoT Core with VPC Endpoints might be a good and relatively simple way to get going. For larger, more demanding operations, a VPN or even Direct Connect could be the way to go. The important thing is to pick a solution that gives you the peace of mind you need, knowing your IoT data is traveling safely and securely.
Frequently Asked Questions (FAQ)
Here are some common questions people often have about securing IoT connections in AWS:
Why is a VPC important for IoT security?
A VPC, or Virtual Private Cloud, creates a private, isolated section within AWS just for your resources. When you connect IoT devices to your VPC, their communication stays within this private network, away from the public internet's potential dangers. This helps keep your data and devices much safer, which is, you know, a very big deal for security.
What's the difference between VPN and VPC endpoints for IoT?
A VPN creates an encrypted tunnel over the public internet, letting your remote devices securely reach your VPC. VPC Endpoints, on the other hand, provide a private connection from your VPC directly to AWS services like IoT Core, without ever going over the public internet. Both are secure, but VPC Endpoints offer a more direct and private path within the AWS network, which, arguably, is sometimes preferred.
How do I authenticate IoT devices in AWS?
Authenticating IoT devices in AWS typically involves using X.509 certificates or AWS Identity and Access Management (IAM) policies. Each device gets a unique certificate or set of credentials. When a device tries to connect, it presents these credentials to prove its identity. This ensures that only trusted devices can connect and send data, which, as a matter of fact, is pretty fundamental to security.