Securing devices that are out there, far away, can feel like a really big challenge, you know? These smart gadgets, often called IoT devices, are everywhere now. They help us do so many things, from keeping our homes warm to watching over big industrial machines. But giving someone access to these devices, especially from a distance, needs to be done very carefully. This is where something called a remoteIoT platform SSH key comes into the picture. It helps make sure only the right people can get in.
Think about it, too. Every day, there is so much new information coming at us. Whether it is learning about sports teams making big changes, like when players get traded, or just trying out a new daily quiz to learn something fun, we are always taking in new details. Just like we learn new things constantly, the ways we keep our technology safe are always changing and getting better. Keeping up with these security tools is, in a way, like staying updated on the latest news or a daily trivia game; it is about knowing what is happening now.
This article will look closely at how a remoteIoT platform SSH key works. We will talk about why it is so important for keeping your connected devices safe. We will also share some simple ways to use it well. This will help you protect your systems from unwanted visitors. It is, you know, pretty important stuff.
Table of Contents
- Understanding the RemoteIoT Platform SSH Key
- How RemoteIoT Platforms Use SSH Keys
- Best Ways to Use RemoteIoT Platform SSH Keys
- Common Questions About RemoteIoT Platform SSH Keys
- Looking Ahead with IoT Security
Understanding the RemoteIoT Platform SSH Key
When you have smart devices spread out in different places, getting to them from afar needs to be very secure. This is where the idea of a remoteIoT platform SSH key really shines. It is, in a way, a very strong lock and key system for your smart devices. This helps keep them safe from people who should not be looking around.
Many businesses and individuals are, you know, putting more and more smart devices into their daily operations. These devices collect information, control machines, and help things run smoothly. Making sure these devices are safe from unwanted access is, apparently, a very big concern for everyone involved. A good security setup can prevent many headaches.
What an SSH Key Really Is
An SSH key, or Secure Shell key, is basically a pair of digital files. One part is called the public key. The other part is called the private key. You put the public key on the device you want to connect to, say, your remote IoT gadget. The private key stays with you, on your computer, so it is just for your use.
When you try to connect to your IoT device, the device checks to see if your private key matches its public key. If they both fit together, like two halves of a puzzle, then access is given. This method is, you know, much safer than just using a username and a password. Passwords can be guessed or stolen more easily, after all.
Why SSH Keys Are Better for IoT Security
For smart devices, especially those out in the field, SSH keys offer a lot of good things. First off, they are very, very hard to break. The way they are made means that guessing the key is almost impossible. This is a big plus for devices that might not have someone watching them all the time.
Also, you do not have to type in a password every time you want to connect. This makes things faster and easier for those who manage many devices. It also means there is no password to accidentally show to someone else, which is, you know, a common problem. This helps to make sure that access is given only when it should be.
Finally, SSH keys can be set up to allow very specific kinds of access. You can, for instance, let a key only run certain commands. This means if a key somehow falls into the wrong hands, the damage it can do is, thankfully, very limited. This adds another layer of safety for your smart device systems.
How RemoteIoT Platforms Use SSH Keys
RemoteIoT platforms are special systems that help you manage and talk to all your smart devices from one central spot. They use SSH keys as a main way to keep these connections safe. It is, in some respects, the main door to your device network. This makes sure that every message sent and received is kept private.
These platforms often have tools built right in to help you create and manage your SSH keys. This makes the whole process much simpler, even for people who are not, you know, security experts. The goal is to make strong security something everyone can use without too much trouble. It is, really, about making safety accessible.
Setting Up Your SSH Keys
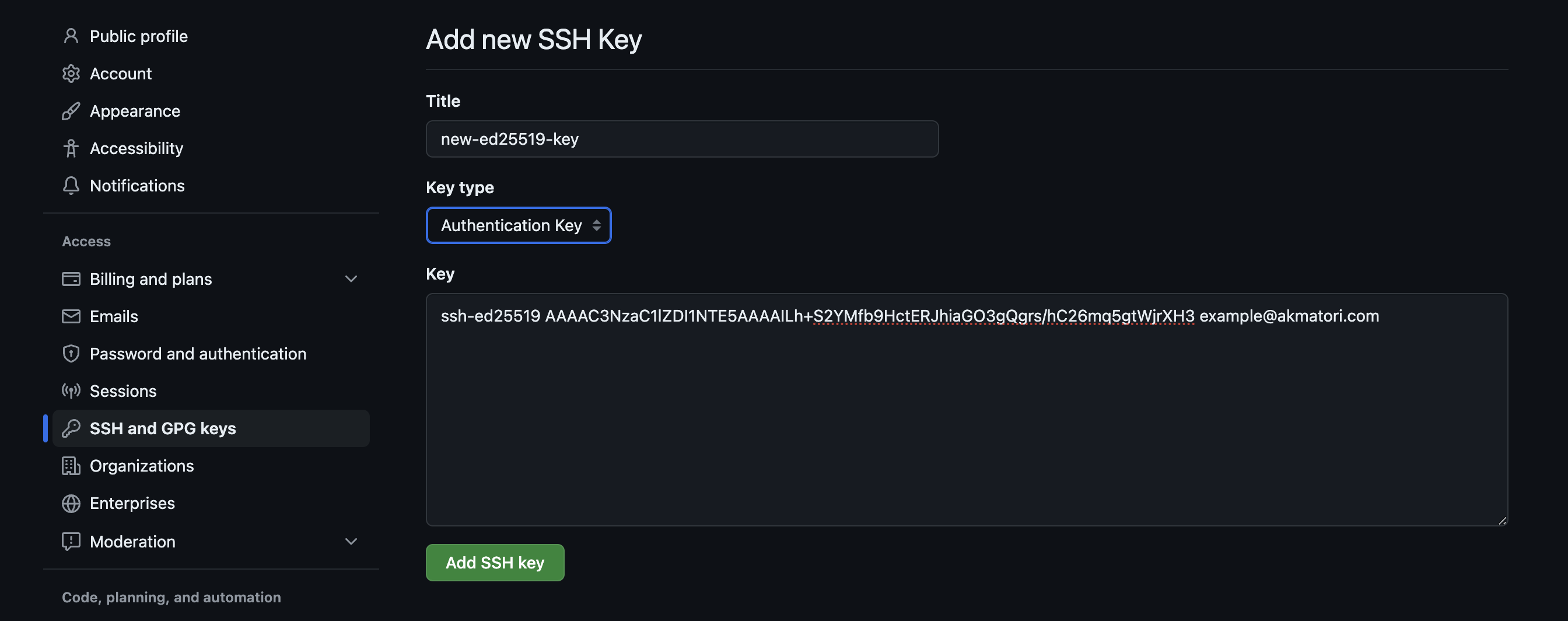
Setting up an SSH key pair is usually a pretty straightforward process. Most remoteIoT platforms will guide you through it. First, you create the public and private key files on your own computer. This is often done with a simple command, or a few clicks in the platform's tool.
Once you have them, you then upload the public key to your remoteIoT platform. The platform then makes sure that this public key gets placed onto your specific smart devices. This step is, actually, pretty important because it sets up the trust relationship between your computer and the device. It is, you know, like giving a specific key to a specific lock.
The private key, remember, stays only with you. It is your personal access pass. You must keep it very, very safe. If someone else gets your private key, they could, unfortunately, gain access to your devices. This is why protecting it is, basically, the most important part of the whole setup. You do not want that to happen.
Managing Keys for Many Devices
If you have just a few smart devices, managing SSH keys might seem easy enough. But what if you have hundreds or even thousands of them? This is where a good remoteIoT platform really helps. They offer ways to manage all your keys from one place. You can add new keys, remove old ones, and see which keys are being used.
Some platforms even let you set up rules for how keys are used. You can, for instance, say that certain keys only work for certain devices. This helps keep things organized and secure, especially in bigger setups. It is, in a way, like having a master key system for all your smart locks. This makes management much simpler.
Automating key deployment is another big advantage. Instead of manually putting a public key on every single device, the platform can do it for you. This saves a lot of time and reduces the chance of making mistakes. It is, quite simply, a more efficient way to handle security at scale. This is, you know, very helpful for big projects.
Best Ways to Use RemoteIoT Platform SSH Keys
Having SSH keys is one thing, but using them well is another. There are some good practices that can make your remoteIoT platform SSH key setup even stronger. These ideas are not hard to follow and can add a lot more safety to your smart device network. It is, in a way, about being smart with your safety tools.
Keeping your security up to date is, actually, a bit like keeping up with the daily news or a popular quiz. You need to check in often and make sure everything is working as it should. This constant attention helps catch problems before they become big issues. It is, really, about staying on top of things.
Keeping Your Private Key Safe
Your private key is, arguably, the most important part of your SSH key setup. It is like the master key to your digital home. You should always protect it with a strong password, also known as a passphrase. This adds another layer of security, so even if someone gets the file, they still cannot use it without the password.
Store your private key in a very secure spot on your computer. Do not share it with anyone, ever. Treat it like your most important secret. Some people even use special hardware devices to store their keys, which makes them even harder to steal. This is, you know, a very good idea for very important keys.
Regularly check the permissions on your private key file to make sure only you can read it. A remoteIoT platform SSH key is only as secure as its weakest link, and often, that link is the private key itself. Being careful here can save you a lot of trouble later on. It is, basically, about being responsible with your access.
Changing Keys from Time to Time
Just like you might change the locks on your house after a while, it is a good idea to change your SSH keys every so often. This is called "key rotation." It means you create a new pair of keys and replace the old ones on your devices and platform. This helps reduce the risk if an old key was somehow, unknowingly, taken by someone else.
How often you do this depends on how important your devices are and how much risk you are willing to take. For very important systems, you might do it every few months. For less critical ones, maybe once a year is enough. Your remoteIoT platform might even have tools to help you do this automatically, which is, you know, very convenient.
Regular key rotation is, in a way, a simple yet very effective security practice. It keeps your defenses fresh and makes it harder for bad actors to keep access if they somehow got in. It is, apparently, a small effort for a big gain in safety. This helps to maintain strong security over time.
Limiting What Keys Can Do
One of the great things about SSH keys is that you can limit what they are allowed to do. You can set up a public key on a device so that it can only run certain commands or access certain parts of the system. This is called "restricted access" or "command restriction." This is, you know, a pretty smart move for safety.
For example, you might have one key that can only read data from a sensor. Another key might be able to restart the device. This means if a key is somehow compromised, the person who has it cannot do everything they want. Their actions are, thankfully, very limited. This helps to reduce the potential damage quite a bit.
This approach is especially useful for different people or different automated systems that need to access your devices. You give each one just the minimum access they need to do their job. This principle, often called "least privilege," is a very important idea in security. It helps keep your remoteIoT platform SSH key setup truly safe.
Common Questions About RemoteIoT Platform SSH Keys
People often have similar questions when they start looking into securing their smart devices with SSH keys. Here are some of the most common ones, with simple answers to help you out.
What is an SSH key used for in IoT?
An SSH key in IoT is used to create a very secure way for you to connect to your smart devices from afar. It helps to make sure that only authorized people or systems can access and control these devices. This is, you know, pretty important for keeping your data and devices safe. It acts like a very strong, digital handshake.
How do I secure my IoT devices remotely?
To secure your IoT devices remotely, you should use SSH keys instead of just passwords. You also need to make sure your remoteIoT platform is set up correctly to manage these keys. Keeping your device software up to date and changing your keys regularly are, arguably, very good steps to take as well. These things help a lot.
Can I use passwords instead of SSH keys for IoT?
While you can use passwords, it is generally not recommended for IoT devices, especially those that are out in the open. Passwords are much easier to guess or steal compared to SSH keys. SSH keys offer a much stronger layer of security and are, in fact, the preferred method for remote access to smart devices. It is, honestly, a much safer choice.
Looking Ahead with IoT Security
The world of smart devices is always growing, and so are the ways we need to keep them safe. A remoteIoT platform SSH key is, in a way, a fundamental tool in this ongoing effort. It provides a strong and reliable way to manage access to your connected hardware. As more devices come online, this kind of security becomes even more vital.
Staying informed about the best ways to protect your devices is, you know, a continuous process. Just like learning new things every day, whether it is about sports or a quiz, keeping up with security practices is key. For more great information on keeping your digital world safe, you can learn more about cybersecurity on our site. Also, to understand more about secure connections, you might want to check out this page about SSH keys in general.
Using SSH keys effectively means you can have confidence in your remote IoT deployments. It means your data is safer, and your devices are less likely to be used for bad purposes. This peace of mind is, you know, pretty valuable. It helps you focus on what your smart devices do best, without constantly worrying about their safety.